Table of Contents
Secure programming language – why is it needed?
Why is using a secure programming language so important? It is a key component of any successful cybersecurity strategy. Secure technology has implications for protecting data, maintaining trust, and achieving compliance. Embracing such technology is a forward-looking investment in the organization’s enduring prosperity and security. A programming language’s security level depends on what we mean by “secure.” No programming language is completely secure by default. However, among the many programming languages available, Java remains a solid choice for developing robust and scalable applications. It is designed to provide security with numerous built-in features such as cryptography, authentication, and public key infrastructure if the code base is written correctly and configured. Therefore, developers must follow secure coding practices, use only trusted libraries, sanitize all input, and implement access control mechanisms to ensure the security of Java applications. We discuss more about these practices later in the article. Now, we will analyze what affects the security of Java when programming applications.Java features that affect application security
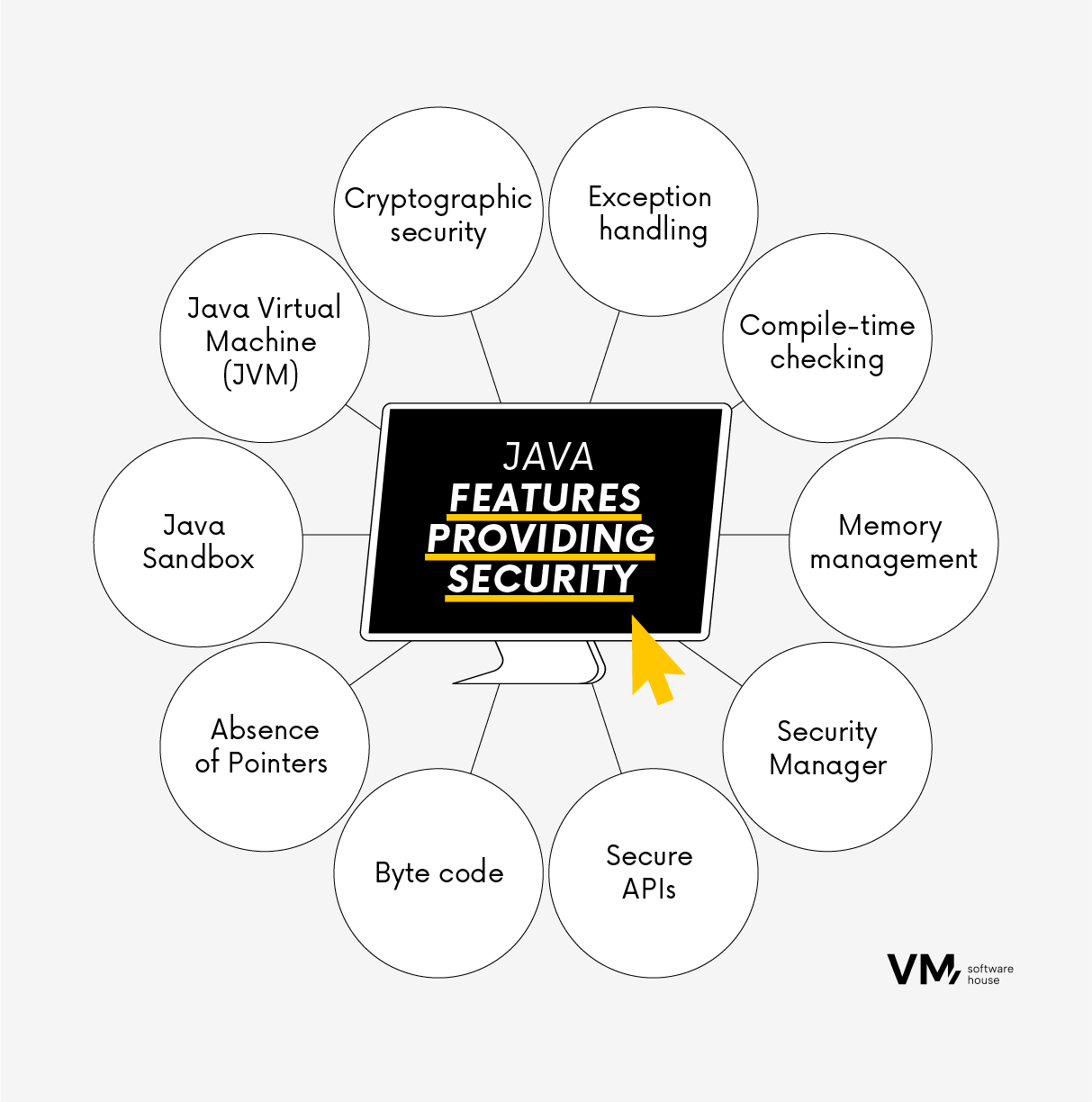
Java is a safe programming language when used correctly and according to best practices. However, as with any technology, the quality of the software depends on various factors, including how it is implemented, configured, and maintained. Here are some reasons why Java is considered a safe technology:- Java Virtual Machine (JVM)
- Sandbox
- No support for indicators
- Byte code
- Security APIs
- Java Class Loader Security Manager
- Memory management
- Checking at compile time
- Exception handling
- Cryptographic Security
What factors can weaken Java security?
As with any other language, the security of Java applications also depends on how they are designed, coded, and configured. Here are some factors that can harm Java application security:- Misconfiguration: Poorly configured Java applications or servers introduce security vulnerabilities in Java, including weak password policies, improper permissions, or unsecured defaults.
- Unsecure coding practices: Failure to follow secure coding practices leaves Java applications vulnerable to common security threats like SQL injection and cross-site Scripting (XSS).
- Outdated software: Using outdated versions of Java or neglecting to update third-party libraries and dependencies exposes applications to known security vulnerabilities.
- Improper input validation: Improper validation and cleansing of user input data can result in security vulnerabilities.
- Lack of security testing: Inadequate security testing, including penetration testing and code reviews, allows security vulnerabilities to go undetected.
- Third-party dependencies: Java applications often rely on third-party libraries and frameworks, making vulnerabilities in these components a risk to the application’s overall security.
- Security Awareness: The security awareness and expertise level among developers and administrators significantly impacts Java application security.
12 important security practices in Java application development
1. Validation of input data Java developers must implement robust input validation to secure data from users or external sources, guarding against security risks like SQL injection and Cross-Site Scripting (XSS). Query parameterization is a key prevention technique. Employing input validation libraries or frameworks, such as OWASP ESAPI, is highly recommended. 2. Cryptography Java offers robust encryption and decryption libraries for safeguarding sensitive data from eavesdropping during transmission or storage. These libraries utilize cryptographic hashing algorithms, enabling secure password storage and authentication without revealing the actual password. 3. Authentication and authorization Authentication: Java frameworks like Spring Security or Apache Shiro enable robust user authentication mechanisms, ensuring only authorized users access sensitive resources. Implement strong identity verification methods, including two-factor authentication (2FA). Authorization: Access control, driven by roles or attributes, dictates who can perform specific actions or access particular data. It guarantees that users only access authorized resources. 4. Monitoring and recording Java applications can log security events and anomalies. Utilizing log analysis systems can help identify unusual patterns and potential security breaches. Intrusion detection systems (IDS) can be employed to create custom IDS solutions or integrate with existing ones for monitoring network traffic and system behavior to detect cyberattacks. Additionally, Java-based vulnerability scanning tools and penetration testing frameworks can pinpoint and rectify vulnerabilities in Java applications, mitigating the risk of exploitation by attackers. 5. Network security: Firewalls and network filters Java is suitable for configuring and managing firewalls and filters to control traffic and block potentially malicious requests. It also supports SSL/TLS protocols for secure network data transmission, ensuring encrypted network communications are shielded from eavesdropping. 6. Security libraries and frameworks Java offers a range of security libraries and frameworks like Bouncy Castle and OWASP Java Encoder, providing pre-built solutions for common security tasks such as cryptography and input/output validation. These solutions encompass secure coding practices like utilizing prepared statements for database queries and escaping special characters to prevent user data from executing as code. 7. Vulnerability scanning and testing Java-based vulnerability scanning tools and penetration testing frameworks, such as OWASP Dependency-Check and Snyk, can identify and mitigate vulnerabilities in Java applications before potential exploitation by attackers – consistent dependency scanning aids in discovering and resolving known security vulnerabilities. 8. Security updates and patch management: Java applications must stay up-to-date with security patches and updates to address known vulnerabilities promptly. This necessitates regular security audits and code reviews to pinpoint and rectify security issues in your codebase. It’s also advisable to implement robust error handling and avoid revealing sensitive information in error messages that attackers could exploit. 9. Secure session management Secure session management safeguards user sessions by using secure cookies, setting suitable session timeouts, and regenerating session IDs upon login. 10. Avoid hard-coding passwords Storing sensitive information, such as API keys, passwords, or encryption keys, in the source code is discouraged. Instead, using environment variables or configuration files with appropriate access controls for managing sensitive data is preferable. 11. Content Security Policy (CSP) Implementing CSP headers is a strategy to mitigate the risk of XSS attacks by specifying the permissible content sources for loading and execution. This can be achieved by configuring HTTP security headers like Content Security Policy (CSP), Strict Transport Security (HSTS), and X-Content-Type-Options. 12. Education and Training Java developers should receive comprehensive training in secure coding practices and cybersecurity awareness to comprehend potential threats and the best practices for mitigating them. By harnessing Java’s capabilities and incorporating security practices into the development lifecycle, organizations can adeptly detect, prevent, and mitigate cyberattacks, ultimately enhancing the overall security of their Java applications and systems.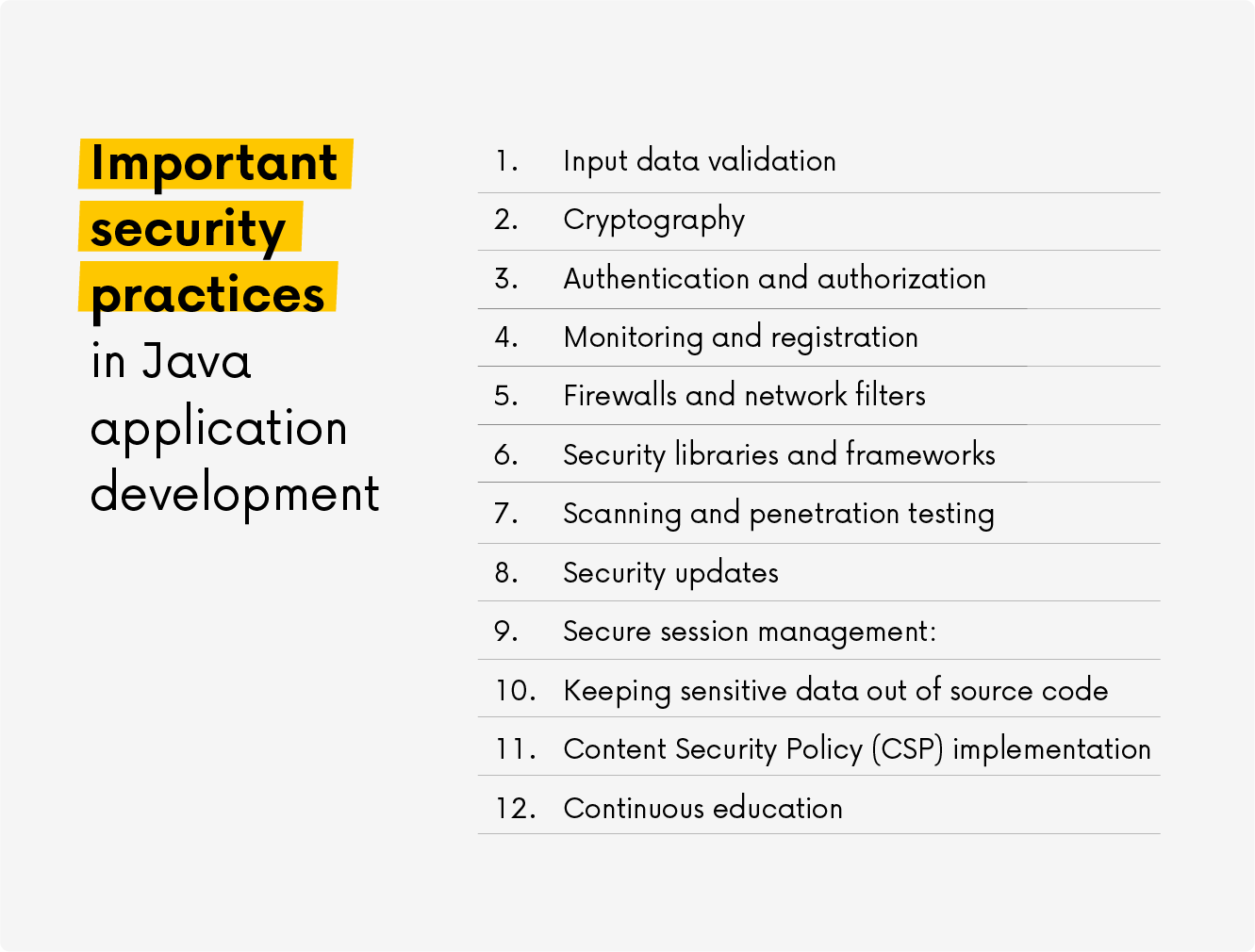
Popular Java security tools
- OWASP Java Encoder
- Spring Security